Introduction
PowerShell is a task-based command-line shell and scripting language; it is designed specifically for system administrators and power-users, to rapidly automate the administration of multiple operating systems (Linux, macOS, Unix, and Windows) and the processes related to the applications that run on those operating systems. It is open source. You can visit its official repository: https://github.com/PowerShell/PowerShell
This chapter will be an overview of how to use PowerShell in red teaming missions .we are going to explore:
- Metasploit and Powershell
- Powersploit
- Powerview
- Nishang
- Empire
- Mimikatz
Metasploit and Powershell:
As a start let’s explore Powershell modules in Metasploit while it comes with many Powershell attack modules:
msf> search powershell
To convert a Powershell script into a malicious executable file you can use msfvenom utility:
>msfvenom -p windows/exec CMD = “powershell -ep <a class="mention" data-id="ngLviZ5rbMDY3Stkh" data-type="Tag" href="/tags/bypass">bypass Hidden -enc [ Powershell <a class="mention" data-id="GNPGKGnfrfFrLL87q" data-type="Tag" href="/tags/script">script Here ]” -f<a href="https://www.peerlyst.com/tags/exe"> exe -o /root/home/ghost/Desktop/power.exe</a</a</a
PowerSploit
PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an assessment. PowerSploit is comprised of the following modules and scripts:
- CodeExecution
- ScriptModification
- Persistence
- AntivirusBypass
- Exfiltration
- Mayhem
- Privesc
- Recon
For more details, you can visit the project Github Repository from this link: https://github.com/PowerShellMafia/PowerSploit
Powerview
PowerView is a Powershell script that gives you the ability to perform many reconnaissance tasks, as follows:
- Users: Get-NetUser
- Groups: Get-NetGroup
- Sessions: Get-NetSession
- GPO locations: Find-GPOLocation
- Active Directory objects: Set-ADObject
- Forests: Get-NetForest
It is a part of the Powersploit project.
Nishang – PowerShell for penetration testing
Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security, penetration testing and red teaming. Nishang is useful during all phases of penetration testing.
Github Link: https://github.com/samratashok/nishang
To import Nishang Modules you can use the PowerShell Cmdlet “Import-Module” if you receive an error message make sure that you have the right privileges
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned
To know more about a module type:
Get-Information <module>
You can now use the power of Nishang using many amazing scripts like:
- Get-WLAN-Keys
- Get-PassHashes
- Get-Information
- Invoke-Mimikatz
- Invoke-CredentialsPhish
Empire
In this section, we are going to explore “The Empire” which is a PowerShell and Python post-exploitation agent maintained by http://www.powershellempire.com/
First before learning how to use this framework we need to make sure that we acquired a fair understanding of some important terminologies.
What is Post Exploitation?
According to The Penetration Testing Execution Standard
“The purpose of the Post–Exploitation phase is to determine the value of the machine compromised and to maintain control of the machine for later use. The value of the machine is determined by the sensitivity of the data stored on it and the machines usefulness in further compromising the network.”
To use the project clone it from the following github repository: https://github.com/EmpireProject/Empire
Clone it and run <a class="mention" data-id="wAGpMrfjv7ykyEKm4" data-type="Tag" href="/tags/sudo">sudo ./setup/install.sh </a
This is the main screen of Empire:
As you can see, this great project contains 3 major components as the following:
- Modules
- Listeners
- Agents
Kali Ninja (https://creator.wonderhowto.com/kalininja/) defines them as the following:
- A listener is a process which listens for a connection from the machine we are attacking. This helps Empire send the loot back to the attacker’s computer.
- A stager is a snippet of code that allows our malicious code to be run via the agent on the compromised host.
- An agent is a program that maintains a connection between your computer and the compromised host.
To check listeners type:
listeners
To use a specific listener type:
uselistener
To take a look at the options type info.
As a demonstration, you can follow this great demo/scenario Post-Exploitation with PowerShell Empire 2.0 performed by “Gus Khawaja” who used this workflow to show the power of The Empire Framework 2.0
Mimikatz
Mimikatz is an amazing C project developed by Benjamin Delpy. It is used generally to extract passwords from memory (plaintexts passwords, hash, PIN code and kerberos tickets). You can download the project from this link: https://github.com/gentilkiwi/mimikatz/releases
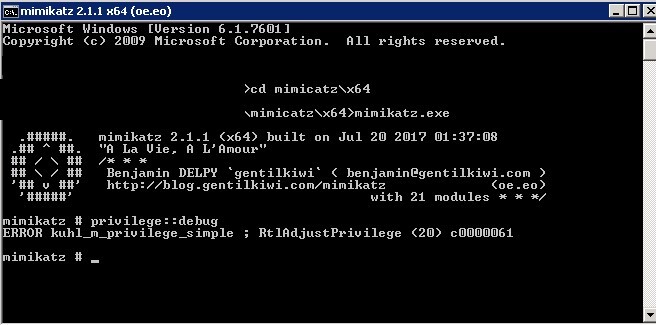
To get the debugging privileges type:
privilege::<a class="mention" data-id="uek5ZKA6p3gvZzFpn" data-type="Tag" href="/tags/debug">debug</a
to extract the hostname type:
hostname
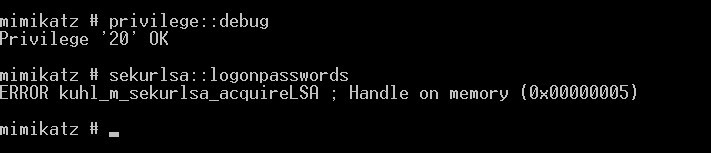
to dump logon passwords you can use:
sekurlsa::logonPasswords full
Summary
In this chapter we took a look at some of the well known powershell projects that help red teamers in their missions.